Friday, July 28, 2017
How To Use Display Filters In Wireshark
How To Use Display Filters In Wireshark
Wireshark is a GUI-based network packet analyser that lets you inspect packet data from a live network as well as from a previously captured file. Although it’s a very powerful tool, a common problem that newbies face is that it displays so much data that it becomes really difficult for them to pinpoint the actual information they are looking for. This is where Wireshark’s display filters help.
Note – If you are completely new to Wireshark, it is recommended that you first go through its basic tutorial.
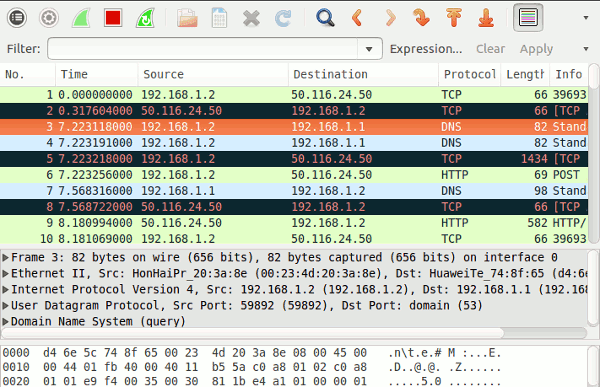
Note that a major part of the GUI is used to display information (like Time, Source, Destination, and more) about all the incoming and outgoing packets. To filter this information as per your requirement, you need to make use of the Filter box present at the top of the window.
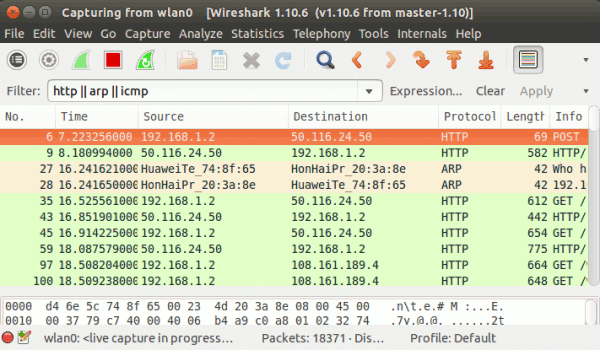
Observe that the Protocol column contains only HTTP entries. If information related to more than one protocol is required, enter the protocol names separated by a double pipe (or a logical OR operator) ||
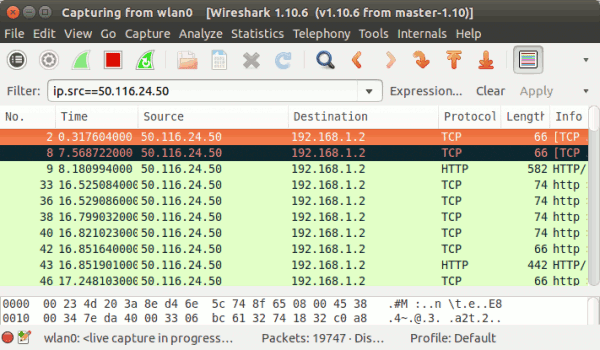
Similarly, use ip.dst to filter results based on destination IP address. To display both source and destination packets with a particular IP, use the ip.addr filter. Here is an example:
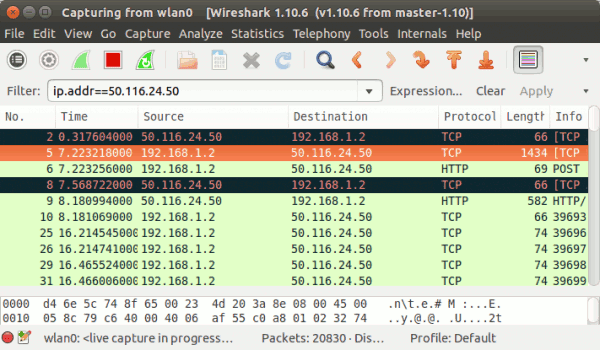
Observe that the packets with source or destination IP address as 50.116.24.50 are displayed in the output.
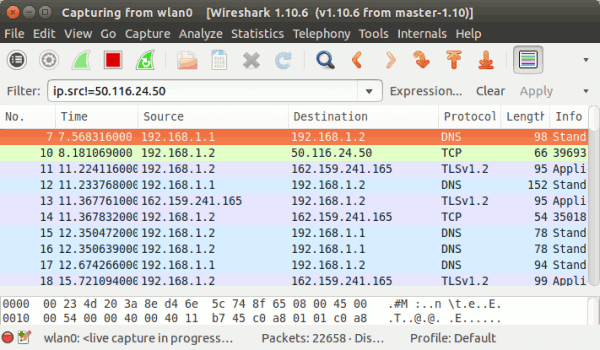
To exclude packets with a specific IP address, use the != operator. Here is an example:
Similarly, you can use tcp.srcport and tcp.dstport to separately filter results based on TCP source and destination ports, respectively.
Wireshark also has the ability to filter results based on TCP flags. For example, to display on those TCP packets that contain SYN flag, use the tcp.flags.syn filter. Here is an example:
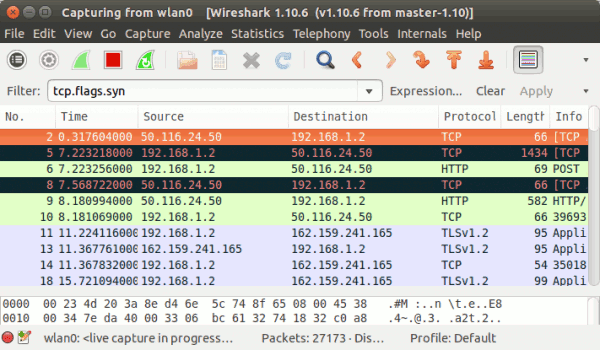
Similarly, you can also filter results based on other flags like ACK, FIN, and more, by using filters like tcp.flags.ack , tcp.flags.fin and more respectively.
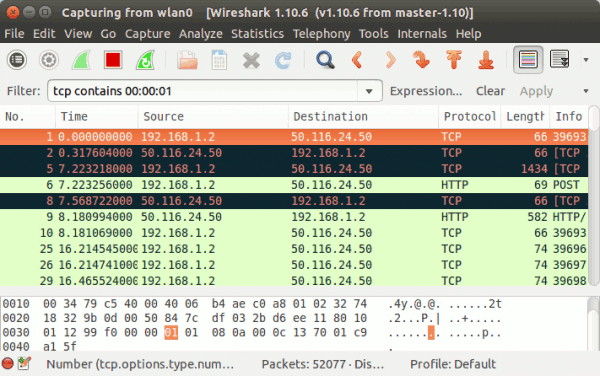
For example, TCP packets containing the 00 00 01 byte sequence can be filtered using the following way:

Moving on, just like you can filter results based on IP addresses (explained earlier), you can also filter results based on MAC addresses, using the eth.addr filter. For example, to see all the traffic coming in and out of a machine with mac address, say AA:BB:CC:DD:EE:FF, use the following filter command:

Note – If you are completely new to Wireshark, it is recommended that you first go through its basic tutorial.
Display Filters

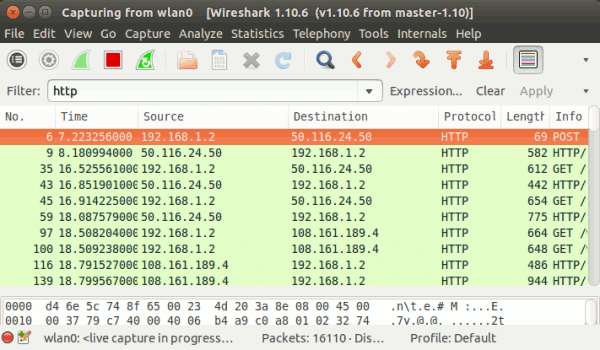
1. Filter Information Based On Protocol
To filter results based on a specific protocol, just write its name in the filter box and hit enter. For example, the following screen shot displays information related to the HTTP protocol
http || arp || icmp

2. Filter Information Based On IP Address
To filter results based on source IP, use the ip.src filter. Here is an example:ip.src==50.116.24.50

ip.addr==50.116.24.50

To exclude packets with a specific IP address, use the != operator. Here is an example:
ip.src!=50.116.24.50

3. Filter Information Based On Port
You can also filter the captured traffic based on network ports. For example, to display only those packets that contain TCP source or destination port 80, use the tcp.port filter. Here is an example:tcp.port==80

Wireshark also has the ability to filter results based on TCP flags. For example, to display on those TCP packets that contain SYN flag, use the tcp.flags.syn filter. Here is an example:

4. Some Other Useful Filters
Wireshark displays the data contained by a packet (which is currently selected) at the bottom of the window. Sometimes, while debugging a problem, it is required to filter packets based on a particular byte sequence. You can easily do that using Wireshark.For example, TCP packets containing the 00 00 01 byte sequence can be filtered using the following way:
tcp contains 00:00:01

eth.addr == AA:BB:CC:DD:EE:FF
I Hope This Article Helps You If You Getting Any Problem Related To This Article You Can Comment By Below Comment Box We Will Help You And If You Need Any Trick Or Software Or Hack You Can Mail Us We Will Try To Give That Article We Happy To Help You All Guys.Thank You Share And Subscribe Us. #Pankaj Patidar Rock
Dont Forget To Like And Follow..

Available link for download